Ninja Tools Access Control Counter

Ninja Tools Access Control Counter
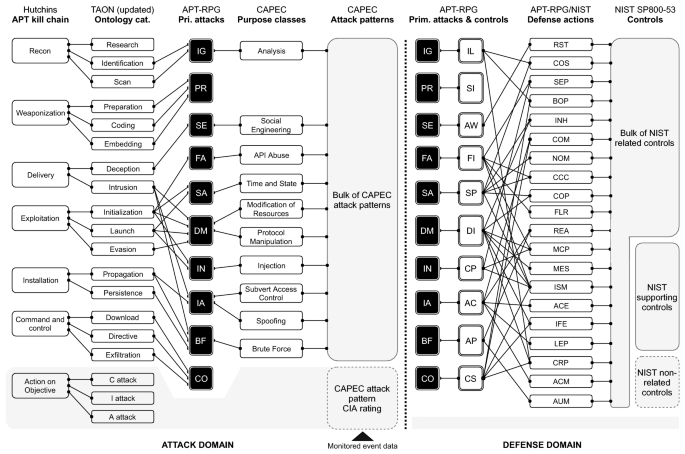
Penquest A Gamified Attacker Defender Meta Model For Cyber Security Assessment And Education Springerlink

Naruto Shippuden Ultimate Ninja Storm Revolution Narutopedia Fandom

Avid Control For Pro Tools Explained Groove3

Ninja Tools Access Control Counter 桜井 乃木坂 桜井 桜井玲香 写真集
Computer Viruses Malicious Logic And Spyware Springerlink
Falcon238jugemjp NINJATOOLS ACCESS CONTROL COUNTER Page load speed analysis 58/100 Normal result;.

Ninja tools access control counter. “The QORTEX Access Control and People Counter products are a key part of the design of various solutions, as they provide highly accurate, reliable and scalable technology that fits the needs of. Dim Ctrl As Control Dim CtrlName As String Dim Counter As Long For Counter = 1 To 10 CtrlName = "P" & Counter Set Ctrl = MeControls(CtrlName) If Counter > MeUsedFields Then CtrlVisible = False Else CtrlVisible = True End If Next BTW, you can use a single line in place of the If block if that makes sense. Rolebased access control in Microsoft 365 We will cover the permissions, roles, and identity updates we have made in the Microsoft 365 admin center and Azure Active Directory Labels Labels Content & Collaboration;.
Access control is a security term used to refer to a set of policies for restricting access to information, tools, and physical locations What is physical access control?. Microsoft 365 1,546 Views 3 Likes 0 Replies Reply. There are two types of access control viz logical and physical Logical access is used to keep intruders and unauthorized users from accessing connections to data, system files, and computer networks On the other hand, physical access control restricts.
Dim Ctrl As Control Dim CtrlName As String Dim Counter As Long For Counter = 1 To 10 CtrlName = "P" & Counter Set Ctrl = MeControls(CtrlName) If Counter > MeUsedFields Then CtrlVisible = False Else CtrlVisible = True End If Next BTW, you can use a single line in place of the If block if that makes sense. What is access rights management?. Microsoft 365 1,546 Views 3 Likes 0 Replies Reply.
Electronic access control (EAC) is the technology used to provide and deny physical or virtual access to a physical or virtual space That space can be the building itself, the MDF, or an executive suite EAC includes technology as ubiquitous as the magnetic stripe card to the latest in biometrics. In this tutorial you will learn what RFID is, how it works and how to make an Arduino based RFID door Access Control with counter and you also see who last a. Access Control that Enables Access control is crucial for protecting physical assets, facilities, and people Yet it is above all enabling technology – helping people to go where they need to go, and do what they need to do, while keeping the organization safe and secure with a minimal management effort.
Traffic access control professionals can now set up Delta Scientific MP5000 portable barriers on concrete, asphalt, compacted soils or vegetation in 15 minutes or less to provide certified M50 stopping power Original models provide M40 protection while the new models stop 15,000 pound (6804 kg) mediumduty trucks traveling at 50 mph (804 kph). This way they fit the overall architecture of a building but also its purpose and the needs of the building users. For gates up to a maximum of ft (49 m) AND 1000 lbs (4536 kg) Part Number LPAPROSW4000XLS.
Occupancy Tracker Tool,Access Management,Capacity Control HeadCounter is a capacity management tool that allows you to keep track of how many people go in and out of events, hotels or any other public spaces you may have You can also share your live occupancy with your customers, so they can decide which is the best/safest time to attend your. The mechanics of restricting access is fairly simple It is not practical to restrict access based on the presence of an existing HSEAS account, but access could be granted based on a specific piece of information, eg, knowledge supplied to those taking a course That knowledge would be a login name and password associated with the web pages. For a control, data from the LastName field is displayed in the control For a report group level, Microsoft Access groups the data on last name =Date( ) 7 For a control, this expression displays a date seven days from today in the control =DatePart("q",ShippedDate) For a control, this expression displays the quarter of the shipped date.
Use the DCount function when you must count records in a domain from within a code module or macro, or in a calculated control You can use the DCount function to count the number of records containing a particular field that isn't in the record source on which your form or report is based For example, you could display the number of orders in the Orders table in a calculated control on a form based on the Products table. S2 NetBox Extreme is a fullfeatured, webbased access control and event monitoring system that supports up to 128 portals Optional system partitioning allows the entire database to be separated into multiple smaller systems for entities such as field offices or tenants. An RFID system consists of two main components, a transponder or a tag which is located on the object that we want to be identified, and a transceiver or a reader The RFID reader consist of a radio frequency module, a control unit and an antenna coil which generates high frequency electromagnetic field.
Network Access Control (NAC) helps enterprises implement policies for controlling devices and user access to their networks NAC can set policies for resource, role, device and locationbased. It seems Access believes the form does not contain a control named txtInput_PM_EN_DRAF T I suggest you the examine names of the controls which Access thinks the form contains I suggest you the examine names of the controls which Access thinks the form contains. Now I need to count the number of villages per district on a monthwise basis on the Report If you have a look at the Report generated currently in the ManeeshMasseyaccdb in your public folder, for example, even though there are 2 villages for Allahabad district, the report shows "1" in all the months in the Report generated.
Raspberry Pi Door Strike Access Control System With Android Tablet Hi everyone,In this Instructable, we will show you how we created our Raspberry Pibased electric door strike access control system, which is comprised of four main parts A hardware subsystem consisting of an electric door strike, a RFID and magn. Support for myQ Community Control Community managers count on LiftMaster's Smart Community Access solutions to provide their communities with trusted and reliable access every day Use our resources below to get support for the cloudbased access control products that help you to conveniently manage every access point of your community. The log and loginput Access Control Entry Options The log and loginput options apply to an individual ACE and cause packets that match the ACE to be logged The loginput option enables logging of the ingress interface and source MAC address in addition to the packet's source and destination IP addresses and ports.
With the form in Design view, insert a text box control Enter the expression in the form =Count (primarykey) as the control's Control Source property The Count () function takes just one. Our cloud management software lets you control access anywhere, anytime Simply login to the online portal to manage users, grant and revoke access and view up to 30 days of activity history Whether you have 1 door or 1,000 doors, in one location or many, everything is at your fingertips on any device. Authentication and Access Control explains the types of errors that lead to vulnerabilities in authentication mechanisms To avoid these mistakes, the book explains the essential principles for designing and implementing authentication schemes you can use in realworld situations Current and future trends in authentication technologies are.
In the Control Source property box, type =Count(*) This expression uses the Count function to count all the records in the report or group even if some fields in some records are null To count records only where a specific field is not null (for example, SupplierName), use the following expression instead =CDbl(Nz(Count(SupplierName),0)). First response 13 sec Resources loaded 47 sec Page rendered 24 sec Total page load time 84 sec Click here to check amazing Falcon 238 Jugem content for Japan Otherwise, check out these. Calculates the number of records returned by a query Syntax Count(expr)The expr placeholder represents a string expression identifying the field that contains the data you want to count or an expression that performs a calculation using the data in the field Operands in expr can include the name of a table field or function (which can be either intrinsic or userdefined but not other SQL.
This way they fit the overall architecture of a building but also its purpose and the needs of the building users. Although this article focuses on information access control, physical access control is a useful comparison for understanding the overall concept. Tamani3net NINJATOOLS ACCESS CONTROL COUNTER 玉手箱ブログは、ドラマや仮面ライダーゴーストなどの特撮番組について、公式HPでの情報を補うような追加情報、解説を書いています。.
Raspberry Pi Door Strike Access Control System With Android Tablet Hi everyone,In this Instructable, we will show you how we created our Raspberry Pibased electric door strike access control system, which is comprised of four main parts A hardware subsystem consisting of an electric door strike, a RFID and magn. Access control systems are an important part of counterterror design and support RIBA’s message of ‘design in security features from the outset’;. Access control is a method of guaranteeing that users are who they say they are and that they have the appropriate access to company data It is a vital aspect of data security, but it has some.
SolarWinds Access Rights Manager is a lightweight rolebased access control software that can help you automate the user account provisioning and deprovisioning process Rolespecific templates are designed to help continuously enforce RBAC security without adding administrative overhead. This bidirectional interface also allows the external system to cancel manually cancellable alarms and issue a remote door commands back to the AC00 access control system AC00 XML Interface The AC00 XML (Extensible Markup Language) interface provides a simple and efficient way to import basic cardholder details into the AC00 access. Adams Rite 8650 Cylinder Escutcheon Trim Kit For 3600, 8500 and 8600 Exit Devices 628 Clear Anodized SKU ADR.
Access Control System Software free download System Mechanic Free, Access 07 Download Access Runtime, Proxy Remote Control Software, and many more programs. Fortunecafeteaniftycom NINJATOOLS ACCESS CONTROL COUNTER Lack of Open Graph description can be counterproductive for their social media presence, as such a description allows converting a website homepage (or other pages) into goodlooking, rich and wellstructured posts, when it is being shared on Facebook and other social media. Data retrieval functions, DLookup, DCount, DSum and more You can use the Data retrieval functions such as DLookUp in an expression or in a VBA function to return a field value in a table The first section focuses on the DLookup function and it's arguments Expr, Domain and CriteriaThis information roughly also applies to aggregate (totals) functions such as DSum and DCount which are.
Access Rights Management (ARM), also known as access control or simply access management, is the practice of ensuring people in an organization have appropriate access to technology resources Good access management tools ensure your users can access areas of your network/systems needed to do their job whilst ensuring other areas are kept offlimits in order. Secure access control can be defined as a system capable of identifying who enters or leaves an area of control and managing the admittance of the person to the building, a specific space or site Different factors for access control Access control is one segment of the physical security equipment and services In terms of access control. You implement table access control with Azure custom roles to either grant access to specific tables in the workspace These roles are applied to workspaces with either workspacecontext or resourcecontext access control modes regardless of the user's access mode Create a custom role with the following actions to define access to table access.
Reexjapanocnknet NINJATOOLS ACCESS CONTROL COUNTER Page load speed analysis 9/100 Poor result;. First response 861 ms Resources loaded 308 sec Page rendered 605 ms Total page load time 323 sec Click here to check amazing Re Ex Japan Ocnk content for Japan Otherwise, check out these. You can use the Count property to determine the number of items in a specified collection Readonly Long Syntax expressionCount expression A variable that represents a Controls object Example The following example uses the Count property to control a loop that prints information about all open forms and their controls.
Service Doors – the “basic” rollup doors suitable for many applications – are also available as WeatherEdge Doors with perimeter weather seals, as Insulated Doors for maximum climate control, or as Ventilated Doors with perforated curtains for the ultimate blend of ventilation, visibility and security High Performance Doors with standard or insulated slats are designed to operate. The Department of Public Safety (DPS) regulates the private security profession in Texas DPS protects the public by conducting fingerprintbased background checks on applicants, investigating and resolving complaints, read more. Leave this field empty if you're human Communicate Instagram @NINJATOOLS Email HI@NINJATOOLSHI@NINJATOOLS.
Access Control Systems for schools When it comes to access control systems for schools;. Access Control, Accessories, Wall Terminal 00 it™, Architectural.

It Campus Security College And School Campus Education Security Security Today
The Future Is Now Our New Client Area And Site Tools Are Going Live Siteground Blog
Versprite S Analysis Of A Vulnerable Window Named Pipe Application

Ninja Tools Access Control Counter 能條愛未 原寸 乃木坂

Ninja Coffee Bars Smoothie Blenders Food Processors Slow Cookers
Naruto Shippuden Ultimate Ninja Storm 4 Beginner Tips And Tricks Naruto Shippuden Ultimate Ninja Storm 4

The Future Is Now Our New Client Area And Site Tools Are Going Live Siteground Blog
Counter Section Ninja Beaver Addon

Protect Your Company Learn How Cyber Criminals Gain Access
Reverse Engineering Attacks 6 Tools Your Team Needs To Know Techbeacon
Best Filmmaking Software And Tools Updated 21

Top 10 Best System Monitoring Software Tools 21 Selective
Github Kdeldycke Awesome Iam Identity And Access Management Knowledge For Cloud Platforms

Ninja Foodi Power Pitcher System Review Rtings Com

This Appliance Replaced Everything On My Kitchen Counter Real Simple
Penquest A Gamified Attacker Defender Meta Model For Cyber Security Assessment And Education Springerlink

Time Management Tools And Techniques To Get More Done Faster

Iface301 Facial Recognition Face Terminal Time Attendance And Zk Access Control Rfid Access Control Time Attendance Iface 301 A530

Ninja Tools Access Control Counter あしゅ 女性モデル 女性

How To Obtain A Guarentee Ninja Tool 2nd Anniversary Tam Naruto X Boruto Ninja Voltage Nxb Nv Youtube
It Campus Security College And School Campus Education Security Security Today

Seo Tools The Complete List 21 Update

Velleman Pem7d C Counter For Mini Ir Security System Walmart Com Walmart Com

5 Current Cyber Attack Techniques And How To Stay Threat Informed

Wireless Security An Overview Sciencedirect Topics

Pdf Cityjson Web Ninja

Naruto Shippuden Ultimate Ninja Storm 4 Beginner Tips And Tricks Naruto Shippuden Ultimate Ninja Storm 4

Privacytools Encryption Against Global Mass Surveillance
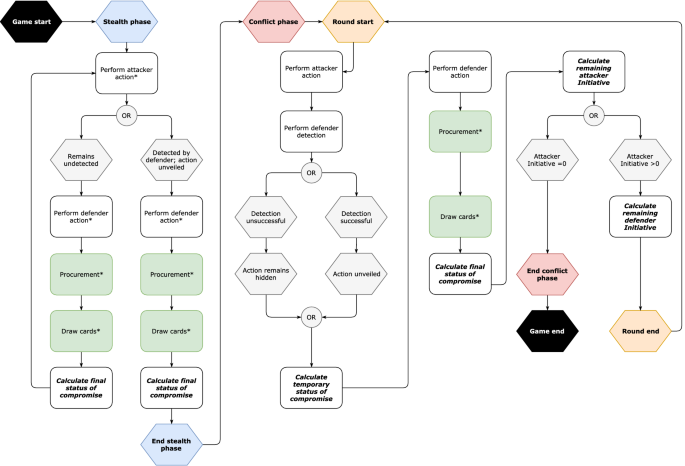
Penquest A Gamified Attacker Defender Meta Model For Cyber Security Assessment And Education Springerlink
忍者バリアーなんて死ねばいいのに Amagrammar Programmer

Ninja Tools Access Control Counter 乃木坂 紅白 乃木坂46 西野七瀬

Ninja Tools Narutoxborutoninjavoltage Wiki Fandom

Ninja Sp101 Foodi 8 In 1 Digital Air Fry Oven Walmart Com Walmart Com

Seo Tools The Complete List 21 Update

So You Got Access To A Nix System Now What Trustedsec

Kbr Wins 92 6m Contract To Reinforce The U S Navy S Counter Unmanned Air Systems Strengthens National Defense

Top 13 Wordpress Project Management Plugins And Tools 21
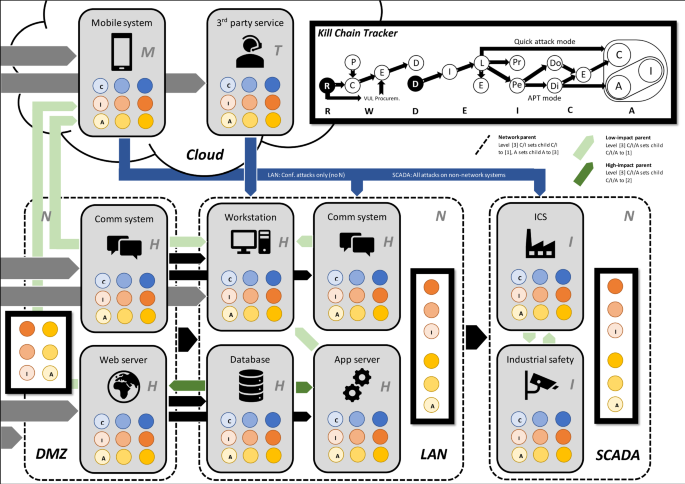
Penquest A Gamified Attacker Defender Meta Model For Cyber Security Assessment And Education Springerlink
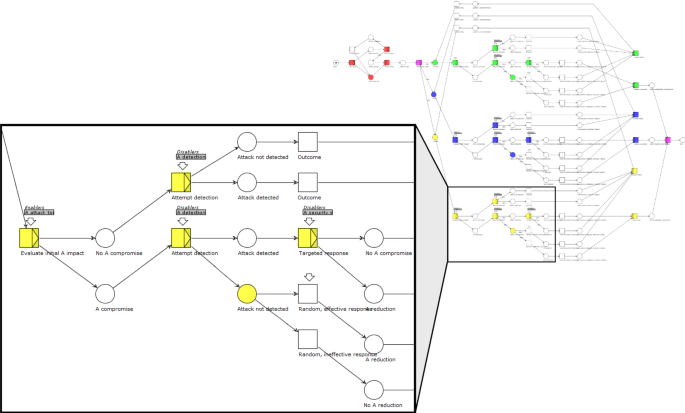
Penquest A Gamified Attacker Defender Meta Model For Cyber Security Assessment And Education Springerlink

Ninja Duo Review Rtings Com

Best Wordpress Security Plugins Compared Free Premium

Ninja Tools Access Control Counter

Amazon Com Ninja Professional Countertop Blender With 1100 Watt Base 72 Oz Total Crushing Pitcher And 2 16 Oz Cups For Frozen Drinks And Smoothies Bl660 Gray Electric Countertop Blenders Kitchen Dining

Ninja Coffee Bars Smoothie Blenders Food Processors Slow Cookers

Welcome To The Mcas Ninja Blog Series Thewindowsupdate Com

Ninja Foodi Digital Air Fry Oven Toaster Air Fryer
Counter Section Ninja Beaver Addon

Naruto Shippuden Ultimate Ninja Storm 3 Narutopedia Fandom

100 Best Network Security Books Of All Time Bookauthority
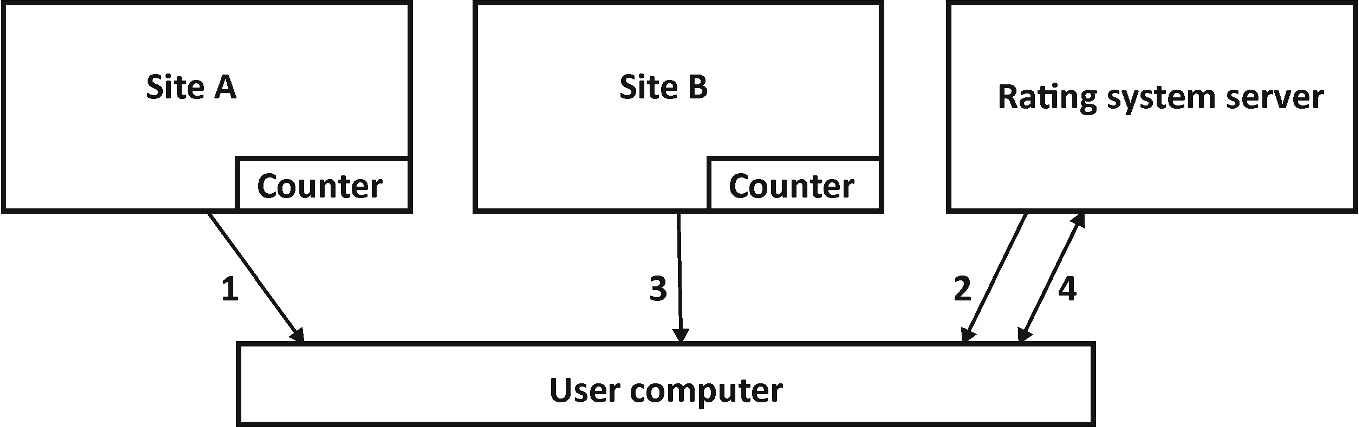
Computer Viruses Malicious Logic And Spyware Springerlink

Welcome To The Mcas Ninja Blog Series Thewindowsupdate Com

Pdf Collaborative Access Control For Critical Infrastructures

Field Types Ninja Forms

Ninja Tools Access Control Counter 衛藤美彩 乃木坂46 衛藤美彩 乃木坂

Best Filmmaking Software And Tools Updated 21
Battlefield Of The Future 21st Century Warfare Issues
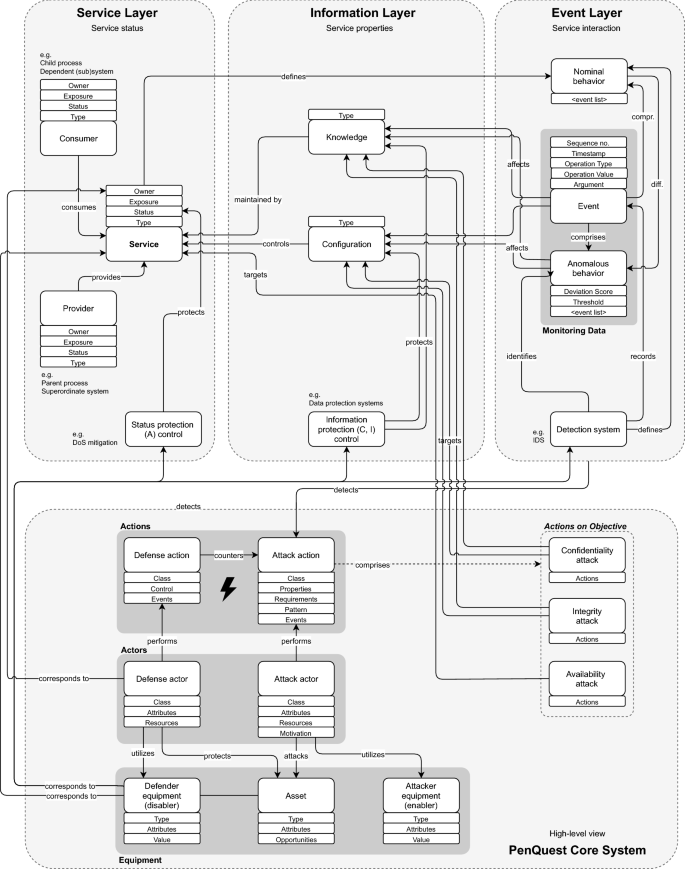
Penquest A Gamified Attacker Defender Meta Model For Cyber Security Assessment And Education Springerlink

Seo Tools The Complete List 21 Update
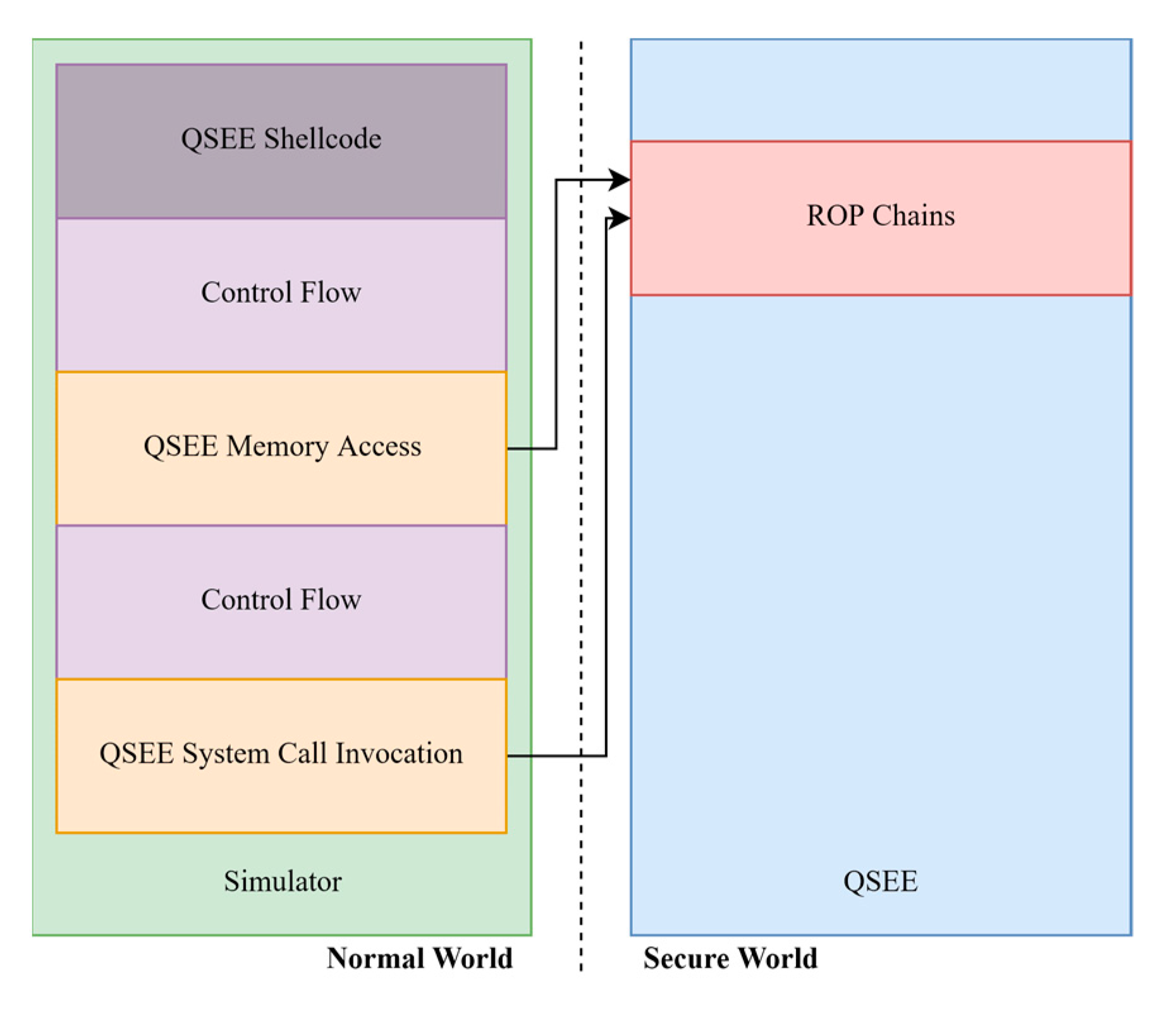
Sensors Free Full Text Building Trust For Smart Connected Devices The Challenges And Pitfalls Of Trustzone Html

Ninja Tools Access Control Counter 久保 久保史緒里 原寸

Ninja Tools Access Control Counter 美容 オルチャンガール 美髪
Best Log Management Tools 51 Useful Tools For Log Management Monitoring Analytics And More Stackify
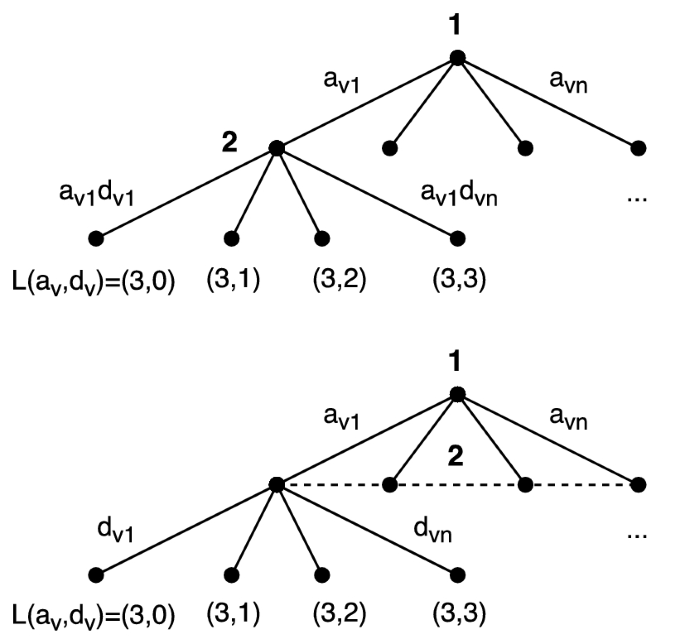
Penquest A Gamified Attacker Defender Meta Model For Cyber Security Assessment And Education Springerlink

Ninja Tools Narutoxborutoninjavoltage Wiki Fandom

Ninja Tools Access Control Counter

Pdf Penquest A Gamified Attacker Defender Meta Model For Cyber Security Assessment And Education

Ninja Tools Access Control Counter 齋藤飛鳥 あしゅ 斉藤飛鳥

Naruto Slugfest Guide Tips Cheats Strategies To Increase Cp Mrguider
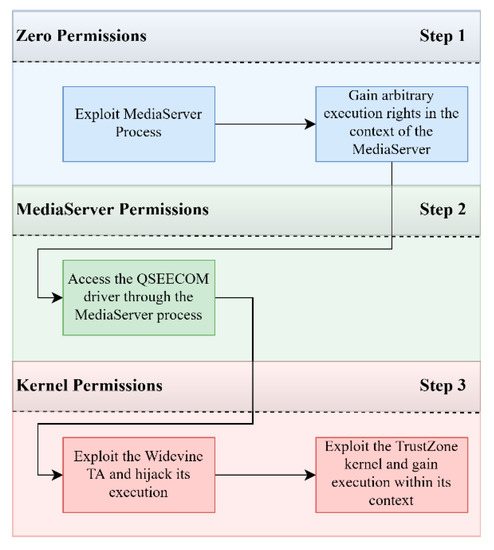
Sensors Free Full Text Building Trust For Smart Connected Devices The Challenges And Pitfalls Of Trustzone Html

Ninja Foodi Digital Toaster Air Fryer With Flip Away For Storage Multi Purpose Counter Top Convection Oven Sp101 19 7 W X 7 5 H X 15 1 D Stainless Steel Black Walmart Com Walmart Com

Security Experts Say Drones Pose A National Security Threat Time

Ninja Professional Plus Kitchen System With Auto Iq Review Rtings Com

Army Selects Countermeasures Against Drones Article The United States Army

Commercial Tool An Overview Sciencedirect Topics

Ninja Tune Wikipedia

Ninja Tools Access Control Counter 紅白 あしゅ 齋藤飛鳥

Katasuke Tōno Narutopedia Fandom
忍者バリアーを簡単にピンポイントで回避 解除 する方法 Firefox アドオン Adblock Plus を利用 pcプチ技能向上委員会

Top 10 Best System Monitoring Software Tools 21 Selective

Amazon Com Sharkninja Ninja Auto Iq Blender Under Counter High Stainless Kitchen Dining

Top 6 Siem Use Cases Infosec Resources

It Campus Security College And School Campus Education Security Security Today
Best Filmmaking Software And Tools Updated 21

Ninja Tools Access Control Counter 中村麗乃 美人 顔 中村

5 Current Cyber Attack Techniques And How To Stay Threat Informed
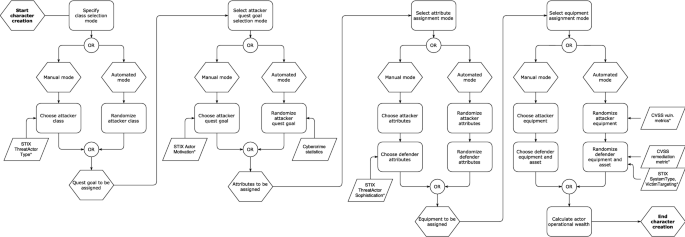
Penquest A Gamified Attacker Defender Meta Model For Cyber Security Assessment And Education Springerlink
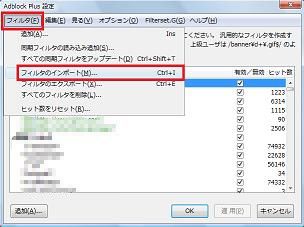
忍者バリアーを簡単にピンポイントで回避 解除 する方法 Firefox アドオン Adblock Plus を利用 pcプチ技能向上委員会

Ninja Tools Access Control Counter 日本の女の子 晴れ着 成人式 髪型
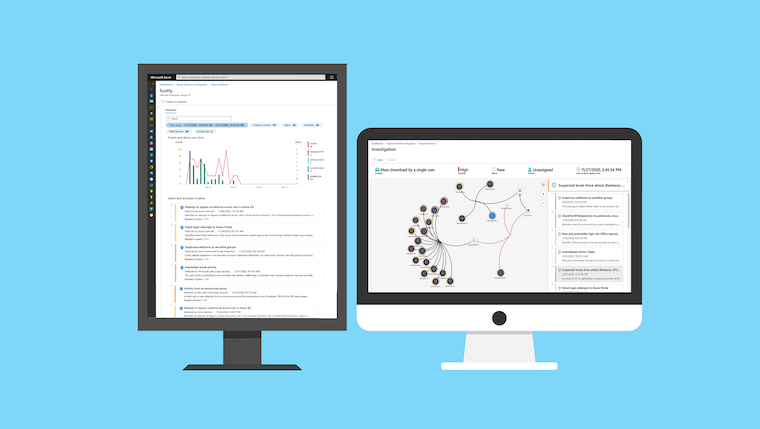
Cloud Architekt Net Identity Security Monitoring In Microsoft Cloud Services

Ninja Tools Access Control Counter 齋藤飛鳥 乃木坂46 齋藤飛鳥 飛鳥

Ninja Tools Access Control Counter 美しいアジア人女性 ビューティープロダクト いい女
Ninja Tools Icons By Romualdas Jurgaitis
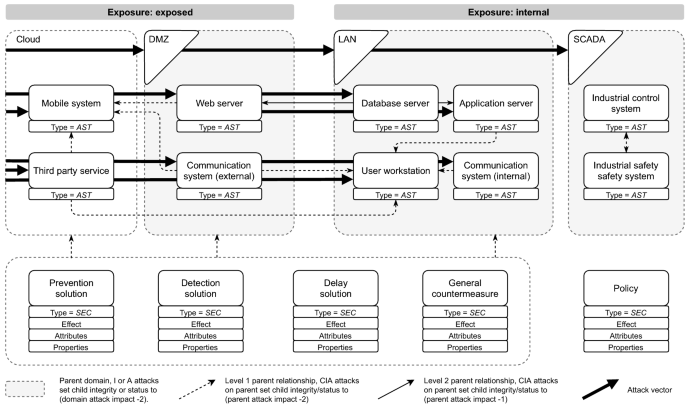
Penquest A Gamified Attacker Defender Meta Model For Cyber Security Assessment And Education Springerlink



